Merge branch 'main' into 'master'
# Conflicts: # README.md
No related branches found
No related tags found
Showing
- Figures/.gitkeep 0 additions, 0 deletionsFigures/.gitkeep
- Figures/ansible.png 0 additions, 0 deletionsFigures/ansible.png
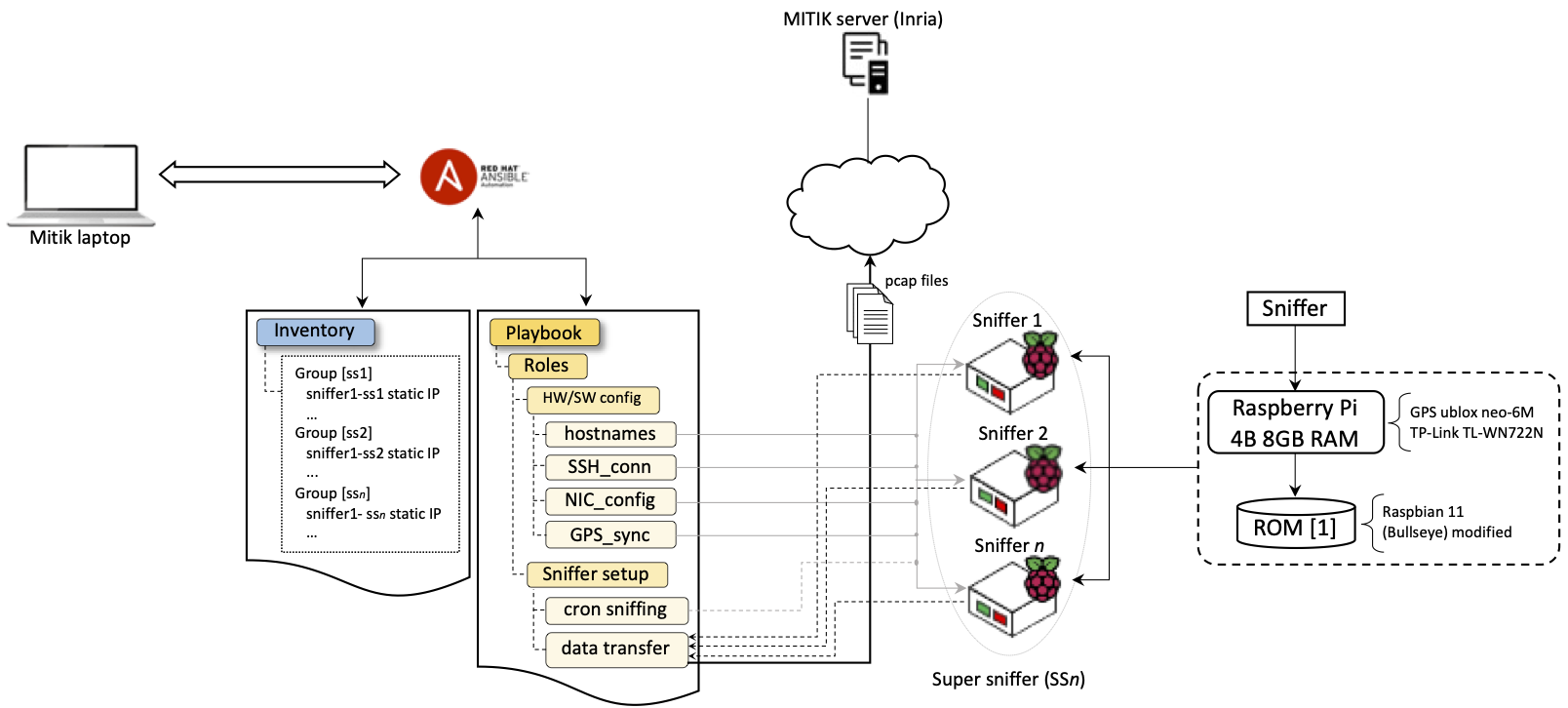
- Figures/ansible_implementation.png 0 additions, 0 deletionsFigures/ansible_implementation.png
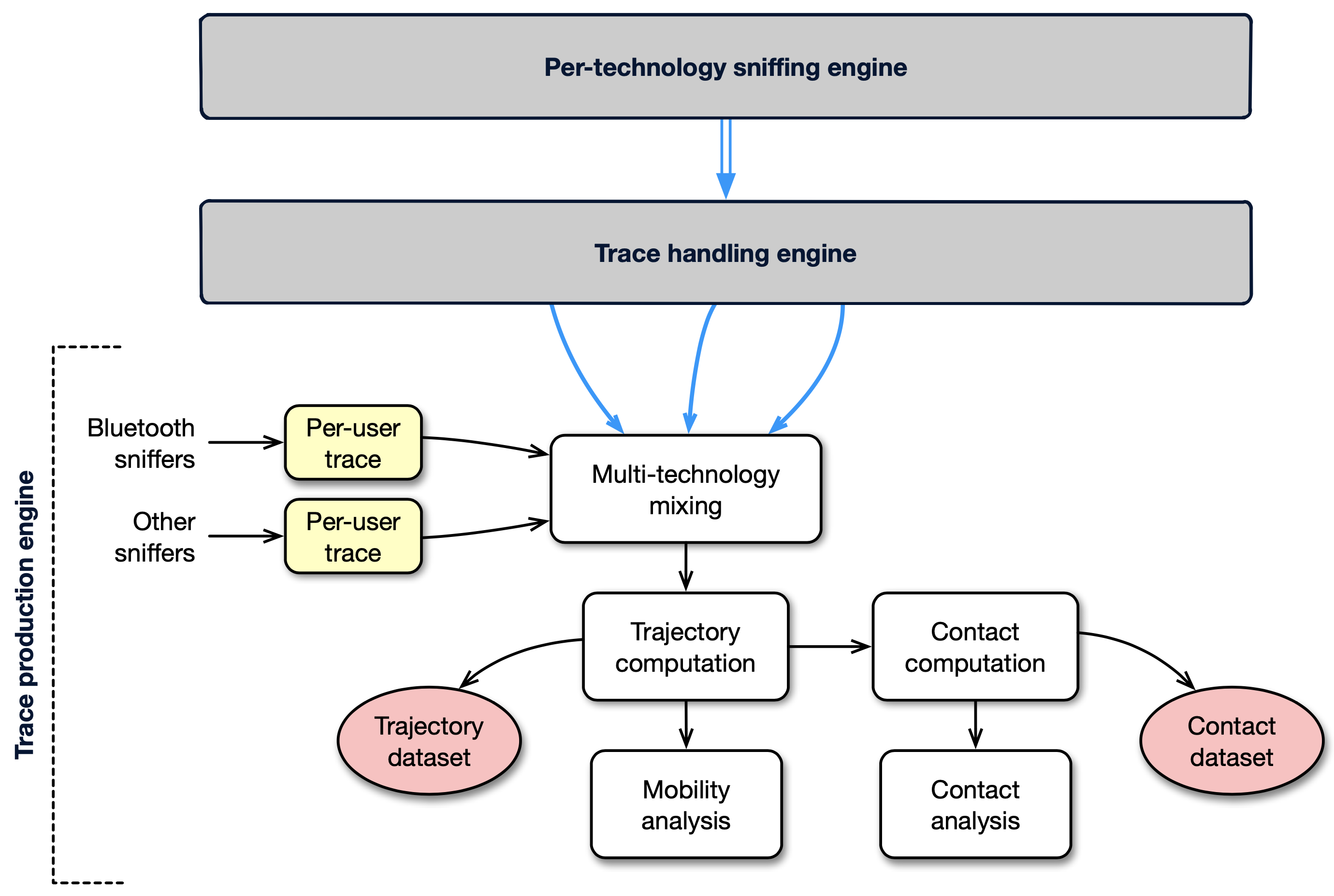
- Figures/architecture.png 0 additions, 0 deletionsFigures/architecture.png
- Figures/gps_conn.png 0 additions, 0 deletionsFigures/gps_conn.png
- Figures/gps_module.png 0 additions, 0 deletionsFigures/gps_module.png
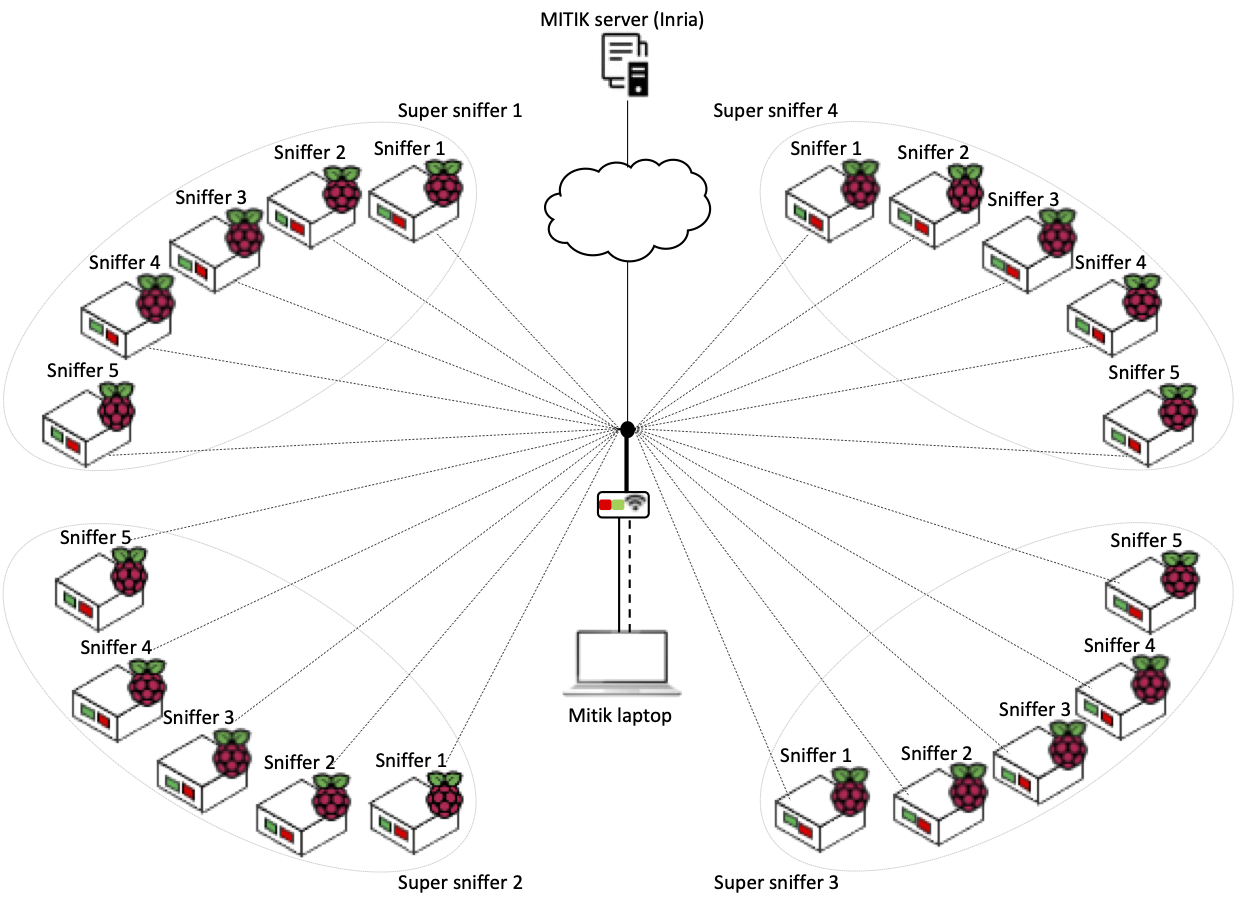
- Figures/mitik_topology.png 0 additions, 0 deletionsFigures/mitik_topology.png
- Figures/module_1.png 0 additions, 0 deletionsFigures/module_1.png
- Figures/module_1_implementation.png 0 additions, 0 deletionsFigures/module_1_implementation.png
- Figures/module_2.png 0 additions, 0 deletionsFigures/module_2.png
- Figures/module_3.png 0 additions, 0 deletionsFigures/module_3.png
- Figures/randomized_MAC.png 0 additions, 0 deletionsFigures/randomized_MAC.png
- README.md 0 additions, 1 deletionREADME.md
- ansible/tasks/README.md 100 additions, 0 deletionsansible/tasks/README.md
- ansible/tasks/playbook_GPS_sync 0 additions, 0 deletionsansible/tasks/playbook_GPS_sync
- ansible/tasks/playbook_GPS_sync.yml 65 additions, 0 deletionsansible/tasks/playbook_GPS_sync.yml
- ansible/tasks/playbook_NIC_config.yml 13 additions, 0 deletionsansible/tasks/playbook_NIC_config.yml
- ansible/tasks/playbook_SSH_keygen.yml 25 additions, 0 deletionsansible/tasks/playbook_SSH_keygen.yml
- ansible/tasks/playbook_data_transfer 25 additions, 0 deletionsansible/tasks/playbook_data_transfer
- ansible/tasks/playbook_hostname.yml 4 additions, 0 deletionsansible/tasks/playbook_hostname.yml
Figures/.gitkeep
0 → 100644
Figures/ansible.png
0 → 100644
69.9 KiB
Figures/ansible_implementation.png
0 → 100644
195 KiB
Figures/architecture.png
0 → 100644
39.1 KiB
Figures/gps_conn.png
0 → 100644
203 KiB
Figures/gps_module.png
0 → 100644
128 KiB
Figures/mitik_topology.png
0 → 100644
372 KiB
Figures/module_1.png
0 → 100644
199 KiB
Figures/module_1_implementation.png
0 → 100644
158 KiB
Figures/module_2.png
0 → 100644
227 KiB
Figures/module_3.png
0 → 100644
378 KiB
Figures/randomized_MAC.png
0 → 100644
51.8 KiB
ansible/tasks/README.md
0 → 100644
ansible/tasks/playbook_GPS_sync
0 → 100644
ansible/tasks/playbook_GPS_sync.yml
0 → 100644
ansible/tasks/playbook_NIC_config.yml
0 → 100644
ansible/tasks/playbook_SSH_keygen.yml
0 → 100644
ansible/tasks/playbook_data_transfer
0 → 100644
ansible/tasks/playbook_hostname.yml
0 → 100644